
Keysight Device Security Workshop 2025

What is the Keysight Device Security Workshop?
The Keysight Device Security Workshop is designed to bring together security professionals, researchers, and engineers to share the latest updates in the embedded security space. Our goal is to engage with current and future users of our Inspector toolset, providing hands-on demonstrations of our hardware and software solutions.
Throughout the workshop, we’ll cover a variety of topics related to embedded device security, including hardware attacks, software-based attacks, and the latest research on embedded devices. We’ll also discuss emerging topics, such as post-quantum cryptography, Artificial Intelligence and OCP Safe, offering insights into testing and protecting devices against real-world attacks. Attendees will have the opportunity to collaborate with security experts from across industries, gain hands-on experience with our tools, and exchange ideas with peers specializing in embedded hardware and software security.
Optional Training Day: Introduction to Side-Channel Analysis & Fault Injection
At select locations, we will be hosting a Training Day before the main workshop. We are offering an exclusive hands-on training day for those new to Side-Channel Analysis (SCA) and Fault Injection (FI). This session will provide a structured introduction to these attack techniques, covering fundamental concepts, common testing methodologies, and basic tool usage. Due to limited seats, participation in the training is limited — please indicate your interest in the registration form below if you’d like to participate.
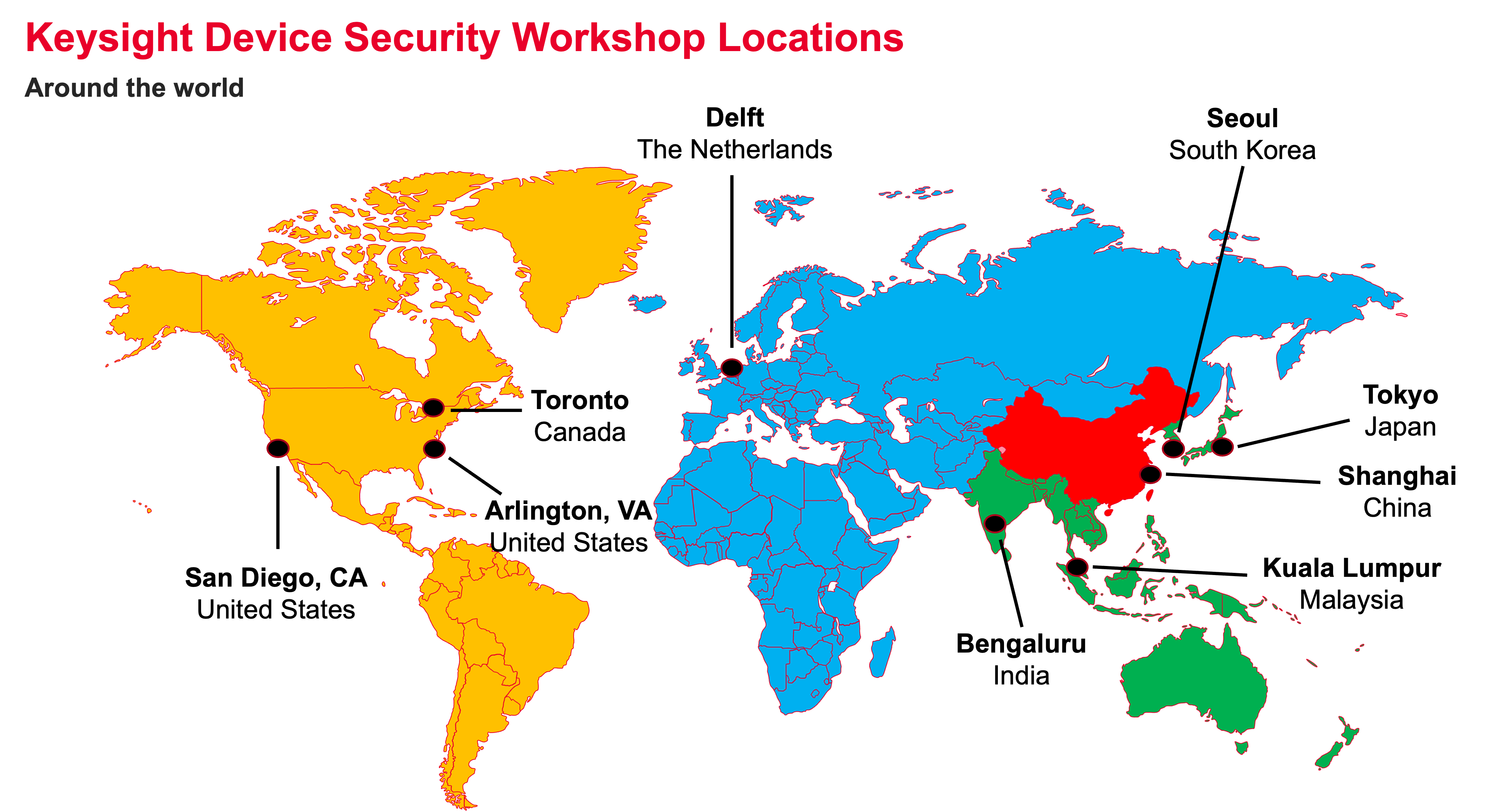
Keysight Device Security Workshop Locations:
Arlington, VA, USA: April 7 & 8
- April 7 (Training Day): Basic training day that covers introduction to SCA & FI, limited availability.
- April 8 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Toronto, Canada: April 10
- April 10 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
- This workshop will take place on the last day of the ICMC 2025 conference.
Seoul, South Korea: April 22
- April 22 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Bengaluru, India: April 24 & 25
- April 24 (Training Day): Basic training day that covers introduction to SCA & FI, limited availability.
- April 25 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
San Diego, CA, USA: May 13 - 14
- May 13 (Training Day): Basic training day that covers introduction to SCA & FI, limited availability.
- May 14 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Shanghai, China (PRC): June 4
- June 4 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Tokyo, Japan: June 6
- June 6 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Delft, Netherlands: June 30 - July 3
- June 30 - July 2 (Training Day): Advanced Raelize Training (more information to come) - limited availability.
- July 3 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Kuala Lumpur, Malaysia: September 19 (After CHES2025)
- September 19 (Workshop): Workshop day consisting of presentations, product demos & discussions from the Keysight Device Security Team.
Workshop Program:
8:30am - 9:00am: Registration / Coffee
9:00am - 10:00am: What's Hot, What's Happened
During this 50-minute talk, Riscure founder Marc Witteman will share his thoughts on recent market developments and gives an insight on his expectations of trends that have a chance to become mainstream soon.
10:00am - 10:30am: Inspector Update - Next Generation Workstation (PXI)
The latest Inspector developments are discussed and demonstrated in this session. Next to that we will present the next generation embedded security testbench. This development of security test devices based on Keysight PXI products will deliver a boost in performance, additional capabilities, and improved user experience. We will cover what is available today and what our roadmap is.
-- 10:30am - 10:45am: Morning Coffee & Snack Break --
10:45am - 11:30am: Post Quantum Cryptography (PQC)
Development of PQC implementations is a necessity nowadays. Usage of PQC algorithms is for example mandated by the US government. In this session we will cover the state-of-the art regarding Post Quantum market developments and will cover side channel and fault injection vulnerabilities for various ciphers: Dilithium, Kyber, XMSS and LMS. Leakage assessment (TVLA) for ciphers using transformations in NTT domain.
11:30am - 12:00pm: Automotive
Achieving UN-R155 and 156 Type Approval: Real-World Experiences and Best Practices. In this session we will cover in what way security labs approach a security evaluation project for a vehicle. We will give insights on the process a typical security lab will follow and though the examples we cover are focused on the automotive industry, concepts can be applied to testing of any other product.
-- 12:00pm - 1:00pm: Lunch Break --
1:00pm - 1:45pm: Invited Speaker (See each location for invited speaker information)
1:45pm - 2:30pm: Artificial Intelligence
We already presented the benefits of using AI to improve FI and SCA test scenarios. For both scenarios Inspector offers modules you can benefit from. Lately though we see more publications on using SCA or FI to attack AI chips to extract secrets, mostly the configuration of trained networks. In this session we will explain how these attacks work and what attackers can gain. Next to that we will also explain how FI can be used to influence the outcome of decisions from AI networks.
-- 2:30pm - 2:45pm: Afternoon Snack Break --
2:45pm - 3:15pm: OCP Safe
We'll provide insights into the Open Compute Project (OCP) Security and Compliance Framework, including the OCP Security Appraisal Framework (OCP SAFE), and how your company can align with these standards to enhance hardware security and resilience. Additionally, we’ll explore the evolving security landscape of hyperscalers and data centers, discussing the unique challenges in securing large-scale infrastructure, mitigating emerging threats, and implementing robust hardware and firmware protections. We will also highlight some attacks that can be categorized as remote SCA or FI.
3:15pm - 3:45pm: Pre-Silicon
We achieved breakthroughs in identifying leakage and root cause in a protected AES implementation. Results from pre-silicon testing correlated extremely well with test results from physical testing on a FPGA . We will provide details on the approach and gains to achieve with this emerging technology.
3:45pm - 4:15pm: RED Certification
We explain how medium assurance product certification like RED can be achieved through chip certification based on the SESIP or ARM PSA schemes. This will leverage the efforts of chip vendors to provide security assurance and enable product vendors to acquire a RED certificate quickly.
4:15pm - 4:45pm: Screaming Channels
Mixed signal chips can be vulnerable for SCA attacks, leaking secret information from a cryptographic operation through a modulated signal over a transmitted carrier wave: WiFi, Bluetooth and now cellular! We will go into the details on how this remote SCA attack works and demonstrate how we were able to find leakage in transmitted cellular signals. For this attack we used several security test devices and Inspector software in combination with Keysight dedicated 5G test equipment.
-- 4:45pm - 5:00pm: Closing & Lucky Draw --
* Please note that the agenda may vary slightly depending on the location. *
Training Programs
1 - Day Introduction to Side Channel Analysis (SCA) & Fault Injection (FI)
Abstract
This 1-day introductory training is designed for participants who are new to Side-Channel Analysis (SCA) and Fault Injection (FI). This session provides a structured introduction to these attack techniques, covering fundamental concepts, common testing methodologies, and basic tool usage.
Through a combination of theoretical lectures and hands-on exercises, attendees will gain practical experience in measuring and analyzing power traces, identifying vulnerabilities, and executing basic FI attacks. This training is an excellent opportunity to build foundational knowledge before attending the main workshop.
Agenda
Lecture: Introduction to Side-Channel Analysis (SCA)
- Fundamentals of SCA
- Power analysis techniques
- Common attack methodologies
Hands-on Exercises: Power Analysis & Measurement Processing
- Navigating through measurements
- Measurement processing
- Alignment of measurements
- Crypto analysis techniques:
- Known Key Analysis
- First-Order Analysis
Lecture: Introduction to Fault Injection (FI)
- Basics of fault injection
- Common techniques and real-world examples
- Challenges and mitigation
Hands-on Exercises: Fault Injection Techniques
- Finding the correct timing
- Tuning glitches
- Working with result plots
Audience
This training is designed for participants with no prior experience in SCA or FI but who are interested in learning about these techniques and their practical applications.
Locations & Dates
- Arlington, VA, USA: April 7th, 2025
- San Diego, CA, USA: May 13th, 2025
- Bengaluru, India: April 24th, 2025
Pricing - Free (registration required)
Prerequisites
- Training will be conducted in an Azure Lab environment
- Participants must be able to make an RDP connection to access the training instance
- Online registration is required before the start of the training
3-days Advanced Training Program
Abstract
3 days program Advanced Training Program Abstract Fault Injection (FI) is often the weapon of choice for breaking into devices when exploitable software vulnerabilities are not known or absent. While FI attacks are nowadays common, typical concepts, methodologies, techniques, and attacks are often not sufficiently understood. While achieving success by simply glitching a target can yield results, it's important to note that this approach alone doesn't facilitate the creation of innovative attacks. In this training, students will experience and appreciate the Art of Fault Injection to exploit the full potential of FI attacks.
Students will experience, with guidance from experts, performing real-world Voltage FI attacks, that were found by Raelize. Students will be use Keysight's Voltage FI tooling in their dedicated training room in Delft, The Netherlands. This training takes students on a multi-day journey during which they perform hands-on exercises (75%) and attend insightful lectures (25%).
Upon completing the training, students will be proficient in executing sophisticated FI attacks on real-world targets using Keysight's Voltage FI tooling. The knowledge gained from understanding the underlying concepts, methodologies, techniques, and attacks, can be used by the students to perform novel FI attacks on other targets of interest.
Agenda
Day 1: Characterization
- Lecture: Target & Tooling
- Lecture: Finding Faults
- Exercise: Bootloader communication
- Exercise: Characterizing the Espressif ESP32 SoC
Day 2: Bypassing Secure Boot
- Lecture: Modeling Faults
- Lecture: Secure Boot
- Exercise: Bypassing Secure Boot of the Espressif ESP32 SoC (CVE2019-15894)
Day 3: Advanced Attacks
- Lecture: Attacking OTP Transfers
- Exercise: Attacking the OTP transfer of the Espressif ESP32 SoC (CVE-2019-17391)
- Lecture: Attacking Data Transfers
- Exercise: Attacking Data Transfers on the Espressif ESP32 SoC (CVE2020-13629)
Audience: Trained Inspector users with experience in SCA/FI testing
Location: Delft – June 30 – July 3 – At Riscure training room
Prerequisites: Keysight (Riscure) hardware will be used and no need to bring your own laptop
Pricing: 3,000 EUR per person for 3 days. Including free access to the workshop Registration through Keysight. Payment is arranged by Raelize directly outside Keysight.
Register for your preferred workshop location by filling out the form below, please also indicate if you would like to participate in one of the Training Days. If you have any further questions, reach out to [email protected].